“Technology is a useful servant but a dangerous master.” - Christian Lous Lange
Imagine a world where email encryption or secure transfer systems, which seem to be invulnerable, can be hacked using quantum computing.
Quantum computing (QC) is a field that is developing quickly. For example, earlier this year, Google built the largest quantum computing chip, a 72-qubit processor.
But what is the main philosophy behind QC?
A Particle in the Quantum World
In the real world, an object can be in one of all the probable states, it can have different energies, or it can be moving at different speeds.
But in the quantum world, there is the concept of superposition, where a particle can exist across all the possible states of position, speed or energy at the same time. So, the results are uncertain and have to be calculated in terms of probability.
Quantum mechanics (QM) is a confusing subject for many. According to QM, a particle can be in two or more places at once, and this is called its quantum state. Every quantum state can be represented as a sum of two or more other distinct states.
To understand this better, take an example from the quantum information processing field. In this sector, there are qubits, instead of classical bits. The qubit “lives” in a state of superposition, a possible combination of the basic states, |0> and |1>.
Contrary to a classical bit, which can only be in the state corresponding to 0 or the state corresponding to 1, a qubit can be in a superposition of both states. This means that the probabilities of measuring 0 or 1 for a qubit are, in general, neither 0% nor 100%, but something between them. Therefore, multiple measurements made in qubits, in identical states, would not always give the same result.
Another paradox referred to the chronological order in which two or more events happen. We have two events: "A happens before B" and "B happens before A," and as per QM, it is possible to prove that both the events can happen first in a probabilistic way.
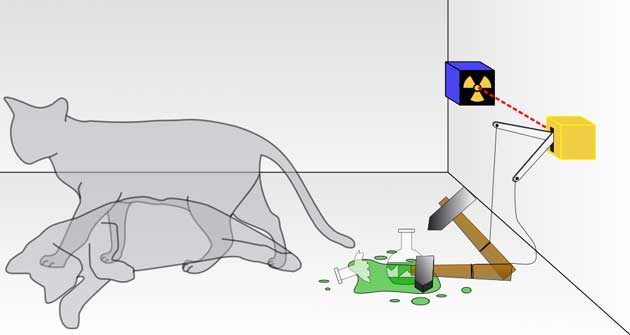
A thought experiment conducted by Erwin Schrödinger to explain quantum mechanics, using everyday objects. (Source: Wikimedia Commons)
Richard Feynman, an important contributor to the quantum theory, said, “Nature is quantum, goddamn it! So, if we want to simulate it, we need a quantum computer.”
This brings us to the question -- can quantum mechanics actually affect our futures?
Cryptography and Blockchain Technology
For secure communication or for private storage of data, organizations or individuals need to make their data unreadable and inaccessible to other users. This has led to the concept of cryptography being considered the main technology for the purpose.
Cryptography is a process which transforms data into an encoded message, that hides the original message, and then allows the receiver to convert the message back to the initial sender. This technique can be traced back to the ancients, with the first documented use dating to 1900 BC in ancient Egypt, with substituted hieroglyphics. Following this, many innovations and discoveries have been made, until now, where intelligent machines are used to produce higher levels of data encryption.
Quantum computing can be used as a threat to cryptography and cybersecurity, in general, and with this technology, information can be processed many times faster too. But what worries scientists the most is the codebreaking and encryption cracking involved.
By design, blockchain is a decentralized technology, a database, which is visible to everyone. A global network of computers uses blockchain technology, and this has an impact on our lives. It is an open, distributed ledger that can record transactions between two parties efficiently, in a verifiable and permanent way. For use as a distributed ledger, blockchain is typically managed by a peer-to-peer network, collectively adhering to a protocol for inter-node communication and validating new blocks.
Blockchain was invented by Satoshi Nakamoto in 2008, the identity of whom is one of the biggest mysteries in the technology world. The pseudonymous creator is estimated to own 980,000 bitcoins, amassed from mining the cryptocurrency in its early days.
Many leading cybersecurity companies use blockchain technology to prevent data tampering. Also, US healthcare companies are beginning to explore this technology for relevant issues. These technologies are threatened by QC, and the types of encryption that companies depend on are no longer considered secure because of the algorithms for codebreaking on quantum computers.
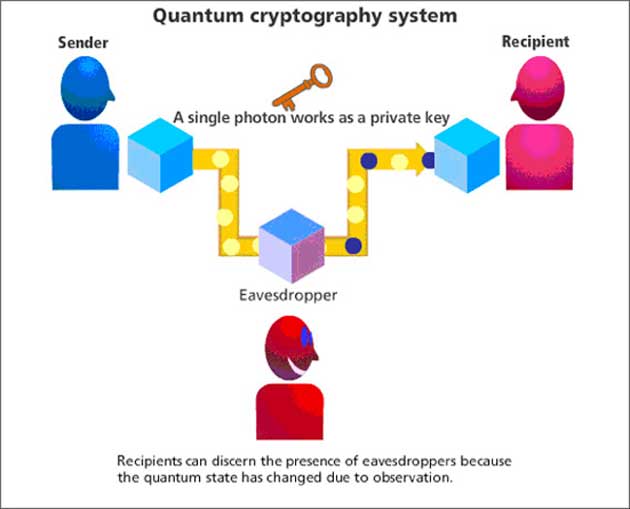
A graphic explaining an interesting concept called quantum cryptography that can potentially solve the problem of compromise of information involved in technologies such as blockchain. (Source: OpenMind)
Public key cryptography is considered is one of the most vulnerable to cracking by a QC, thus putting bitcoin investments at a high risk.
As the director of IBM Research, Arvind Krishna, mentioned, “Quantum computers will be able to instantly break the encryption of sensitive data protected by today's strongest security.” He also warned, "Anyone that wants to make sure that their data is protected for longer than 10 years should move to alternate forms of encryption now."
However, this could, very well, take more than five years because of the advances in quantum computing technologies as well.
In the end, every coin has two sides. If we assess the potential risks through extensive research, then our technologies and people can be protected.
Quantum computers are a technological revolution and can take our communication to a higher level. It is up to us if we evolve the science in a direction that will bring benefits and notable innovations in the future.
Top Image: The role of quantum computers in cryptography. (Image Source: makeuseof.com)
References
1. Jonas DeMuro, 2018. What is cryptography [Online] Available at: https://www.techradar.com/news/what-is-cryptography
2. Sarah Rothrie, 2018. How cryptographic algorithms and hashing keep blockchain secure [Online] Available at: https://jaxenter.com/cryptographic-hashing-secure-blockchain-149464.html
3. Brian Curran, 2018. What are Cryptographic Signatures? Complete Beginner’s Guide [Online] Available at: https://blockonomi.com/cryptographic-signatures/
4. Garry Hilson, 2018. Quantum Computing Is Mathematically Better, But Not Always [Online] Available at: https://www.eetimes.com/document.asp?doc_id=1333900







No comment