Those interested in the evolution of transistor technology may be aware of the memristor. These products were developed, some years ago, in an effort to contribute to the world’s migration from purely digital to analog computing. This process involves the creation of the true artificial synapse, a form of computing that can handle super-binary forms of data and its processing.
Unfortunately for the memristor, it was seen as too cumbersome and power-hungry to form the basis of any next-generation electronics. Also, memristor processing is known to be incredibly difficult to replicate; in other words, they have been effectively un-hackable.
Therefore, these modules may have a role to play after all – in the device security of the future.
Memristors: The Forgotten Next-Gen Components
Memristors are hybrids of a resistor and a memory module, which initially was a place for them as the sub-units of synaptic computing, soon after their invention.
However, subsequent research found that their scaling, power consumption, and cost-effectiveness was difficult to refine in a short time.
Therefore, many engineers and data scientists looked for alternative modules for neural and neuromorphic computing. For example, the transistor-less epitactic SiGe architectures, which form a new kind of RAM, maybe more convincing candidates for the true artificial neuron.
On the other hand, memristors also offer many advantages, which include a source of randomness at the hardware level. This could be used as a barrier to cloning-based hacking, in which whole data networks can be forged, in fine detail, by hackers, and then exploited to gain access to information or a system.
Various domains that memristors can be applied to. (Source: EDGEFX.US)
A team of researchers, collaborating across institutions in California, Romania, and Australia has published a paper in a 2018 issue of Nature Electronics to this effect. This group, led by Hussein Nili of the University of California (Santa Barbara), asserts that memristors can function as a kind of black box for a system. To this end, they constructed simple memristor circuits to act in this way for a single function.
The Memristor Circuit as Security Primitive
The security researchers reported that this memristor barrier had an average uniformity and diffusivity of 50%. Its lowest bit error rate was also approximately 1.5%.
In addition, the memristor's new circuits were reported as being tunable (due to also being analog); their conductance could be changed and reset in response to changing security requirements. These electrical components can also retain their resistance parameters, which allows them even more flexibility in the barrier circuits they form.
All in all, memristors' current and voltage could change frequently and randomly, making their properties extremely hard to predict, which is often necessary for hacking purposes.
Nili and his colleagues say that memristor circuits are power-efficient in some capacity. In any case, their costs in this area may be worth the cybersecurity potential they represent. The circuits are also likely to be able to beat the algorithms that go into ‘learning’ a network in order to hack them.
Under normal circumstances, a bad actor would have to possess only partial access to a network, extrapolate the rest using machine learning, and then, exploit it. Under memristor-enhanced conditions, however, the actual network could have mutated far enough away from the observed conformation, for such measures to be useless, by the time they can be implemented.
Additionally, memristor circuits can be used to generate keys and identifiers that are at least as individual and unique as fingerprints. They could be used to authenticate and authorize devices, components or objects. Again, memristor-based keys would be extremely difficult to forge or mimic.
Barriers to Memristor Integration
Despite these encouraging findings, memristor technology is still not advanced enough for ready inclusion into next-generation systems, and definitely not in those of today.
Nili also observed that the industry adoption of these modules has slowed to a crawl as so many leaders in this area have turned their attention to alternatives.
On the other hand, the security advantages may well rationalize the expenses involved in the development of full memristor integration. For example, manufacturers may have to count arrays for their circuits into the designs now. However, these arrays will have to be designed (and standardized) beforehand.
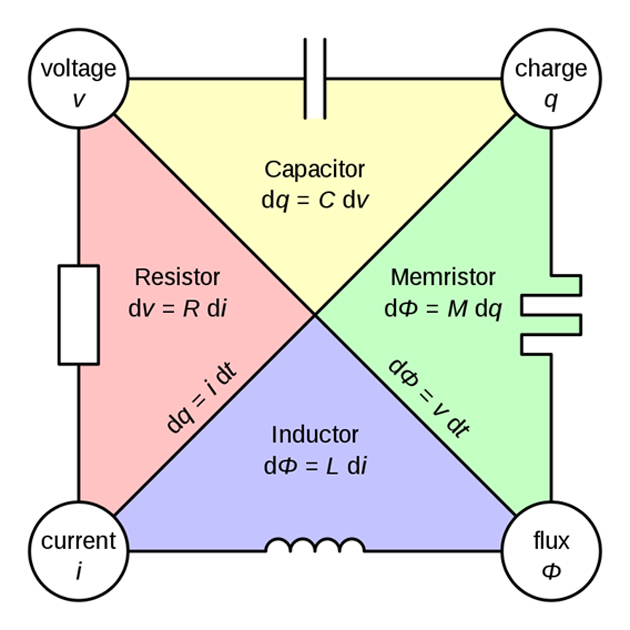
How a memristor may act in a simple circuit. (Source: Parcly Taxel — Travail personnel @ Wikimedia Commons)
Overall, the ideal solution for cybersecurity is within our grasp, but still out of reach.
Memristors have been developed in response to increasing interest and demand for neural computing. However, more effective alternatives prevented their graduation to the integrated-circuit stage. But it seems as though that discarding memristor technology in this way was a considerable mistake.
Circuits made of these modules could pose a significant barrier to hacking by network-counterfeit. In addition, this device could make crime, based on the cloning of circuits or electronic keys, much more difficult.
Now that memristors have a distinct potential role in next-generation computing, their evolution may be interesting to follow.
Top Image: We may all have to become more familiar with the ‘memristor’ symbol soon. (Source: Omegatron; Electrical schematic was created with the Electrical Symbols Library)
References
A Curious, New Hardware Fix for Cybersecurity Vulnerabilities, 2018, hcanews, http://www.hcanews.com/news/a-curious-new-hardware-fix-for-cybersecurity-vulnerabilities , (accessed 10 Jun. 18)
Transcending The Transistor: New Study Towards True Artificial Neuro-computing, 2018, Evolving Science, https://www.evolving-science.com/information-communication/transcending-transistor-artificial-neuro-computing-00676 , (accessed on 10 Jun. 18)
H. Nili, et al. (2018) Hardware-intrinsic security primitives enabled by analogue state and nonlinear conductance variations in integrated memristors. Nature Electronics. 1:(3). pp.197-202.






No comment